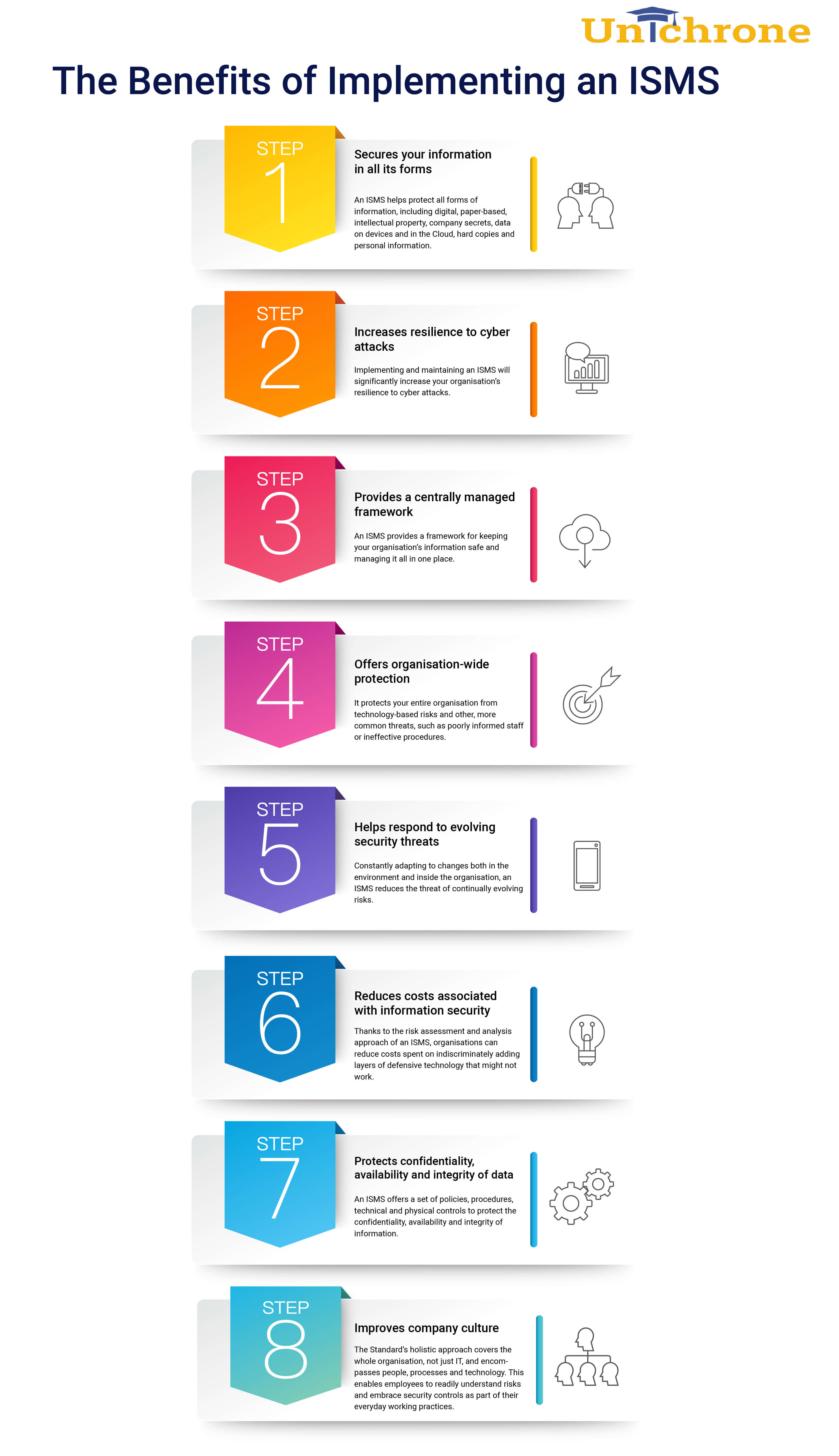
Need to know more on the benefits of Implementing an ISMS into an organization? Here are the top 8 benefits that any organization can gain by Implementing Information Security Management System (ISMS). ISMS helps to safeguard the data nearest to accuracy with regular reviews and analysis.
Jump ahead to
What Is An ISMS?
“Information Security Management System” or ISMS is a documented framework comprising an array of security enforcement. It allows protective access to client information by monitoring the user’s activities. This structure governs business practices in a manner such that the corporate assets remain confidential. It ensures that an enterprise is hardly prone to external or internal vulnerabilities.
Advantages Of Implementing An ISMS
An ISMS shields an enterprise against all possible odds that may result in its absence. Cybercrime has reached its peak due to the constant sharing of data in enormous quantities across the worldwide web. Here are the benefits assured by an ISMS established within an organization.
Flexibility
A single ISMS is sufficient for protecting data of diverse kinds. These are data related to intellectual property, personal information, and company secrets. No matter in whichever form data is present, whether in hard or digital copy, it stays protected. ISMS is the one-stop solution for an organization’s multiple headaches regarding data security.
Enhanced resilience
An organization develops greater resilience by implementing ISMS within its work culture. Employees already observing the regulations of this information security management framework become well-versed in them. This enables them to quickly recover from the aftermath of any data security hazards in no time.
Reduced threats
An ISMS introduces the discipline of using risk-preventive measures while executing business operations. Organization management and employees become addicted to avoiding data security threats at every stage. Subsequently, their chances of encountering cyber-attacks drop considerably.
Cost-effectiveness
It may sound surprising that if a website stops functioning even for half a day, it will lead to financial losses for its owner. Then it is needless to say the losses a company would face on the occasion of keeping its website shut for a week or month. ISMS makes provision for cost-effective solutions to start running the site at the earliest possible. So, the enterprise remains free from unwanted financial burdens.
Improved work culture
ISMS involves every member of an organization in observing its enforcements one way or the other. With time these activities grow on individuals, and they are unable to do away with them. This gives rise to an improved work environment making the organization gradually climb up its success ladder.
Full-fledged security
The physical and technical controls of ISMS cater to every data protection requirement possible. Its procedures and policies ensure the privacy of corporate data based on their confidentiality levels. These policies prevent strangers from meddling with the information that they do not require for work purposes. The procedures establish legal obligations regarding the exploitation of private data of clients or consumers.
Overall protection
ISMS is an all-rounder that directly or indirectly improves all operating faculties of an organization. Data security management helps in keeping several technology-related risks at bay.
How To Implement An ISMS In An Enterprise?
The aforementioned benefits make ISMS implementation profitable for every organization in the long run. Given below is a step-by-step guide for ISMS implementation.
- ISMS implementers must provide a clear idea about the end objectives the organization desires to accomplish.
- Before establishing this structure it is important to decide on the type of information to be protected. It depends on the expectation of the company’s trustees, stakeholders, or clients.
- Acquire absolute knowledge of information storage areas and individuals who have access to them.
- Prepare an inventory comprising every possible data asset of an enterprise. It can be associated with databases, hardware, software, or physical locations.
- Including a risk analysis system is the final step that is done by observing the injunctions of ISO 27001.
- Risks are approached in two systematic ways- vulnerability and scenario-based approaches.
- Ranking the priority of a risk in terms of its severity is included too, within these steps.
Conclusion
An ISMS implementation is a success when it is aligned with ISO 27001 information security regulations. All these efforts are worth the uninterrupted functioning of an organization. Business owners start having fewer nightmares of cyber attacks’ consequences. Instead, they get more time to focus on the core business areas. Anyone who is interested in learning about ISO 27001 standards can enroll in ISO 27001 Lead implementer Certification Training. Training helps candidates to gain deeper understanding of the ISO 27001 standard and the implementation procedures. This enables them to use their acquired knowledge and expertise in practical applications.
Below are few more resources related to Information Security Management System.
Why Should a Company Need an ISO 27001 Certification?